October is National Cybersecurity Awareness Month (NCSAM) , is an annual initiative to raise awareness around cybersecurity issues and to empower everyone to protect your personal data in our highly digitized world.
- Week 1: Phishing and E-mail Security
- Week 2: Multi-factor Authentication
- Week 3: Passwords and Password Managers
- Week 4: Importance of updating all software
Cybersecurity Awareness Month Webinar Webinar
The UH InfoSec team kicked off Cybersecurity Awareness Month with a webinar covering various topics including:
- Phishing and E-mail Security
- Multi-factor Authentication
- Passwords and Password Managers
- Importance of updating all software
Webinar Recording [UH Login Required]
Webinar Slidedeck [UH Login Required]
Week 1 – Phishing and E-mail Security
Be Rude!
…to Phishers and Cybercriminals
By responding to their emails and texts, you are doing exactly what they want.
What is Phishing?
It is an internet scam in which cybercriminals use emails to trick you into performing an action such as downloading a file with malicious software or revealing personal information like banking credentials, SSN, etc.
Don’t Fall for Phishing:
Stop.
Examine. Ask.
Report.
S.E.A.R. the Phish
How to Recognize a Phishing Email
- It comes from an address you don’t recognize: If the email address of the sender is not automatically displayed, you may need to click on the caret symbol (^) under the sender name to view more details or click on the sender’s name to view the sender’s email. If the email claims to be from a legitimate business but uses an incorrect email address, chances are it’s a phishing email. If you want to double-check the message’s legitimacy, consider contacting the sending using another method (if they used email, try calling the company).
- It asks for personal information: Most legitimate business will never ask for personal information (SSN, passwords, credit card information, banking information, credentials, etc.) via email.
- A strong sense of urgency or repercussions: The phishing email may threaten the termination of your account if you don’t respond or follow out the email’s instructions.
- An incredible deal: If your email contains an unbelievable offer, it’s probably a phishing email.
- The suspicious email contains a link or a file: The file attached to the email may contain malware and the link could send you to a fake website and steal your information. To check where a link will send you while using your desktop browser, hover your mouse over the link and the link’s address will appear in the left corner. On mobile, tap and hold the link for a few seconds. A popup containing the link’s address will appear.
The email might also ask you to click on a link and login to view a confidential document stored in Google Drive or other cloud service. Double-check the website you are on by checking the URL bar.
Protect Your UH Account
- Set up Multi-Factor Authentication on your UH account by visiting this article: https://www.hawaii.edu/askus/1758
- If you believe your UH account might have been compromised, change your UH account password here: https://www.hawaii.edu/username/
- If you received a phishing email on your UH Gmail account, report it to ITS by following these instructions: https://www.hawaii.edu/askus/898
Week 2 – Protect yourself
…with Multi-Factor Authentication (MFA)
Single factor authentication is not enough, the world is driven by the Internet where your information is stored by various companies. Data breaches of those companies may expose potential passwords for hackers to utilize against you!
What is MFA?
Multi-factor authentication adds an additional layer of security for accounts, applications, data, and systems to require two or more credential types to authenticate. This can be a combination of passwords, PINs, biometrics, or a unique one-time password sent via SMS or generated by a physical hardware token/authenticator app. The three main credential types of MFA are something you know, something you have, and something you are. Passwords and PINs are something you know as you have set them, and have it memorized or stored. Unique one-time passwords are something you have that can generate the code for you like a hardware token or mobile application. Lastly, biometrics is something you are as it requires fingerprints, iris scans or other biometric indicators that only you can produce.
MFA helps slowdown attackers
While enabling MFA is a great additional layer of security for your accounts, there are still ways to bypass the mechanism such as SIM swap attacks or malware to intercept SMS codes or Voice prompts, attacks on the vendor’s applications, or new techniques such as MFA Fatigue attacks. MFA fatigue attacks is a way of attackers exhausting users of MFA Push notifications by spamming authentication attempts until a user eventually accepts. There are also phishing or voice phishing attacks in which attackers impersonate a victim’s helpdesk or IT support in an attempt to get them to accept a prompt. Just because you enabled MFA doesn’t mean you are safe, securing your accounts require users to always be diligent when authenticating.
What do you do if you are a victim of MFA fatigue attacks or notice suspicious MFA prompts?
- Do not accept any prompts! The point of these spam authentication attempts is to wear out the user and force them to accept to make it stop. Don’t do what they want and deny all requests. If these happen at night, silence your phone and take action first the in the morning!
- Change your password! If you are getting MFA requests it means your credentials are compromised. The attacker successfully authenticated to your account, but needs your approval to gain access. You should change your password as soon as possible, and if your password is similar to any other accounts you use change them as well as once they know a structure it will be easier for them to guess variations. To change your UH account password visit: https://hawaii.edu/username
- Do not respond to suspicious calls or text asking you to accept! While MFA fatigue attacks is one way to pressure a user to accept one of them, they are usually accompanied by SMS or voice calls trying to impersonate your “IT support” and get you to accept. If you receive a SMS message, ignore it and never click on any links as they may try to infect you with malware to intercept your codes. If you receive a suspicious call from someone claiming to be “IT Support” for your company or vendor support, tell them you will call them back.
- Contact the IT support of the company you are getting prompts for! Never use links or contact information you receive in text or voice messages. Your best option to contact the appropriate people is to look on the company’s website for contact information. A lot of times people fall victim by connecting with operation centers setup specifically to gather more information or get you to do a task on their behalf. Once you obtained the appropriate contact information notify the company that your account has been compromised so they can take the appropriate actions to identify the scope of the attack
- Check if you have been any recent breaches! A successful authentication from an attacker means your credentials were either easy to crack or it was compromised through phishing or a breach. You should always check accounts as well if you used similar password syntax as the compromised account. You can type in your email address to this website to check if you’ve been compromised: https://haveibeenpwned.com/ .
Remember to…
- Enroll in MFA whenever it’s available to you!
- Work
- Personal
- Mobile
- Avoid SMS verification methods as much as possible! It is the weakest verification method due to number portability attacks, attacks against the carrier network, and malware that can intercept your codes.
- Be vigilant when reviewing authentication attempt notifications
- Never respond to messages or calls from “IT Support” asking you to approve or provide your code. Ask them you could call them back and then call the company IT Support directly.
Protect Your UH Account
- Set up Multi-Factor Authentication on your UH account by visiting this article: https://www.hawaii.edu/askus/1758 .
References
MFA Fatigue: Hackers’ new favorite tactic in high-profile breaches: https://www.bleepingcomputer.com/news/security/mfa-fatigue-hackers-new-favorite-tactic-in-high-profile-breaches/
Week 3 – Passwords Made Easy
Short and Simple Passwords are Easy to Crack
- Specialized computers can attempt 100 trillion passwords a second.
- Common “gaming computers” can attempt 100 million passwords a second.
- A short and simple password such as “John123” can be cracked in a fraction of a second.
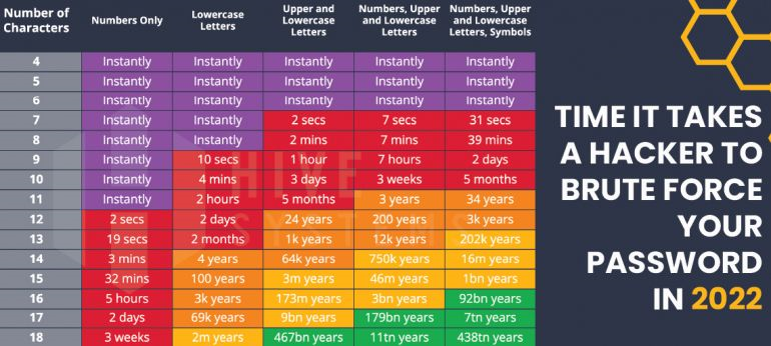
Source: https://www.hivesystems.io/blog/are-your-passwords-in-the-green
Always Use Long and Complex Passwords
- Length is the primary factor in determining password strength. Passwords 6 characters or less can be cracked instantly regardless of complexity requirements.
- Adding numbers, uppercase, and special characters makes it significantly harder to crack passwords.
- 8-12 characters with uppercase, lowercase, numbers, and special characters is the minimum recommendation.
Criminals are Clever
- Criminals use human psychology and trends to automate password prediction.
-
Common predictable password-making techniques
- Word + number + special character (i.e.
Poke2799$) - Word + birthday/zipcode (i.e.
Kona05271986orManoa96822) - Character replacement (i.e.
$up3r_L0n6_P@ssw0rd!) - Keyboard walking i.e.
1qaz2WSX3edc4RFV5tgb

- Word + number + special character (i.e.
Correct Horse Battery Staple
-
Instead of remembering a long password, instead remember a combination of words
- “Correct Horse Battery Staple” = 28 characters long (including spaces)
- Numbers and special characters can be added to meet complexity requirements (Don’t just add them to the
end).
-
The four words should be completely unrelated or it will be easy to guess. Examples of bad usage:
- “Apple Orange Banana Watermelon” = Related words
- “This Is Too Easy” = Short words that form a sentence
- “Words Words Words Words” = Repeating words
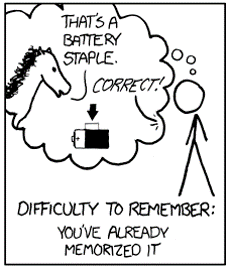
Source: https://xkcd.com/936/
Password Managers
- Store all your passwords securely in one location.
- Memorize one very strong password and implement multi-factor authentication to ensure your passwords are secure.
- Make sure to back up your password on paper or on a secure drive!
- Passwords are encrypted so companies never see the passwords.
- Password managers can be used to generate strong passwords that you don’t have to remember. Just copy-paste from the manager!
- Examples: Bitwarden, 1Password, LastPass, Dashlane, KeePass (offline only).
Learn about password managers here: https://www.hawaii.edu/infosec/resources-tips/password-manager/
Bad Ways to Store Passwords
- Online files such as google sheets, google docs etc. can be easily exposed and are unencrypted.
- Local files such as Word documents, text documents, Excel sheets etc. are often unencrypted and can be stolen.
- Notes on mobile devices can be read by malicious apps and malware.
- Avoid storing passwords in your browser. Malware can extract all your passwords to gain access to your accounts.
What about “Security Questions”?
- Attackers often phish security questions or use public resources to gather information.
- Questions such as “What was the name of your first pet?” and “What is your mother’s maiden name” are easy to find out or guess.
-
Instead, use new passwords to answer the security questions.
- Your password manager can generate passwords to use!
- Example: What is your mother’s maiden name =
uG~"*0hX0bO;&D[H4J=
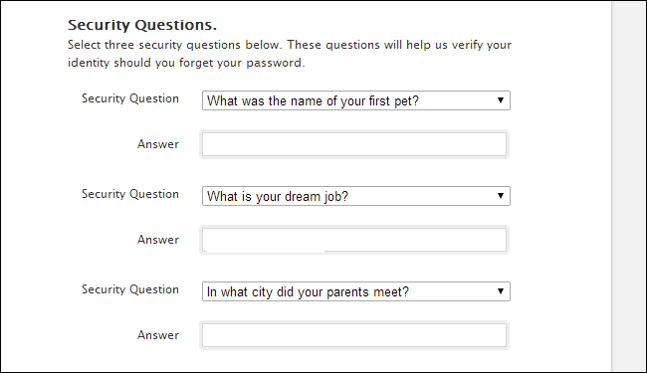
Never Reuse Passwords
- Attackers don’t just “guess”. They often use large lists of previously exposed passwords.
-
Attackers generate new lists using variations. For example, the password “
Coconut123@” can be changed to…Pineapple123@Coconut321@Coconut123!@321tunocoC- …and many more
Have you been Pwned?
- Check if your accounts have been previously compromised by checking your email.
- https://haveibeenpwned.com/
As a reminder…
-
Avoid using your UH email to signup for services
- Increase risk of being targeted by phishing campaigns
- If you lose access to your UH email, you will not be able to recover your accounts!
- Don’t share your passwords with other people
- ITS will never ask for the password of your account.
Week 4 – Importance of updating all software
As hundreds of vulnerabilities or identified weaknesses are reported & found each day, it’s important to be vigilant with updating all software. The reason for this is that cyber criminals look to exploit or leverage any weakness that may be present on a system. Malicious activities such as data exfiltration, ransomware deployment & more are examples of malicious activities one can encounter when avoiding or delaying updates frequently as updates are released to fix or patch vulnerabilities. Due to this, updating all software is one of the easiest and most effective ways to protect yourself.
Best Practices
- Update often and as soon as possible.
- Enable automatic updates for all software (if available).
- Only download updates from trusted sources.
- Upgrade all software that has reached its “End of Life” (no longer supported).
- Beware of fake update messages when browsing the web.
Flyer



