Virtual Server: How to Protect Your Server with Duo MFA on SSH (Linux)
- Email itscs@hawaii.edu to inform us that you'd like to setup Duo MFA on your Linux/Red Hat virtual server, and we will add your server to our Duo environment. Please verify that you are enrolled in Duo MFA. See Getting setup for Multi-Factor Authentication (MFA) for more information.
Please include the following information in your request:
Hostname or VM name
IP address
NOTE: This is only provided to virtual server customers hosted under ITS Managed Services.
- We will filedrop you three keys, which are required in the Duo configuration on the server.
Integration key
Secret key
API hostname
-
Before you begin with the installation, please ensure that a local account matching your exact UH username has been created on the server. Duo MFA will be configured to push on UH usernames, so any username that does not match an existing UH username (i.e., "admin" or "user") could fail, thus locking you out of the server.
Please also note that using variations of your username (i.e. "jdoe" vs "johndoe") for the server account that does not match your own username could potentially lock another person out of using Duo MFA, if they have that as an existing UH username.
-
On your server, first install the OpenSSL development headers and libraries by running
yum install openssl-devel
- Create /etc/yum.repos.d/duosecurity.repo with the following contents:
[duosecurity]
name=Duo Security Repository
baseurl=http://pkg.duosecurity.com/RedHat/$releasever/$basearch
enabled=1
gpgcheck=1
- Execute the following shell commands:
# rpm --import https://duo.com/DUO-GPG-PUBLIC-KEY.asc
# yum install duo_unix - Once duo_unix is installed, edit login_duo.conf (in /etc/duo or /etc/security) to add the integration key, secret key, and API hostname from your Duo Unix application (replace the highlighted text with the keys that were sent to you).
[duo]
; Duo integration key
ikey = INTEGRATION_KEY
; Duo secret key
skey = SECRET_KEY
; Duo API hostname
host =API_HOSTNAME
Additional options in the login_duo.conf file can be edited by referencing this page: https://duo.com/docs/loginduo#duo-configuration-options -
As a regular user, test login_duo manually by runningIf everything is set up correctly, you should see a Duo prompt:
$ /usr/sbin/login_duo
Note: On some systems, you may need to run/usr/local/sbin/login_duo
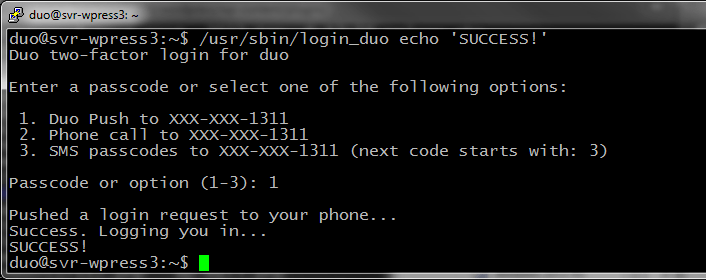
-
To protect remote access via SSH, you will need to edit your sshd_config (usually in /etc or /etc/ssh) to add the following line (NOTE: This is only available with OpenSSH 4.4+):
ForceCommand /usr/sbin/login_duo -
Restart SSH by running "systemctl restart sshd"
-
Make a test SSH connection to your server to ensure that the Duo push prompt comes up.
Before installing and configuring Duo MFA, please ensure you have accounts created on your server matching UH username accounts. Duo MFA will be configured to push on UH usernames, so any username that does not match an existing UH username (i.e., "admin" or "user") could fail, thus locking you out of your server.
Please also note that using variations of your username (i.e. "jdoe" vs "johndoe") for the server account that does not match your own username could potentially lock another person out of using Duo MFA, if they have that as an existing UH username.
See Optional on bypassing accounts in Duo MFA.
Optional:
If you want to exclude usernames from being prompted for DUO MFA:
- Create a group (ie. duoexclude) in /etc/group and add those usernames to this group.
- Add the following to the bottom of the /etc/ssh/sshd_config file
Match Group *,!duoexcludeForceCommand /usr/sbin/login_duo
- Add "groups = *,!duoexclude" to /etc/duo/login_duo.conf
- Restart SSH.
For more references and information, please see this link: https://duo.com/docs/loginduo



